We’ve taken several important steps on the road to making “MITM-proof communication” on your favorite websites possible.
- We released the first version of DNSChain, the blockchain-based DNS resolver (fully compatible with canonical DNS).
- We launched the first public DNSChain server. Its 600 lines of CoffeeScript have been running flawlessly since February 6th.
- We launched the okTurtles forums and #dnschain IRC channel.
dot-DNS makes secure JavaScript apps possible

Figure 1. Firefox believes that “The connection to this website is secure.”
Unfortunately, so do most users.
As detailed in the okTurtles paper, today’s internet faces a security crisis. HTTPS and the technology on which it is based (SSL/TLS) are incapable of securing all connections because the mechanism TLS uses for authentication is insecure.
This means today’s JavaScript apps are at the mercy of the security provided by web browsers, which are incapable of distinguishing a secure SSL/TLS connection from one that’s being man-in-the-middle‘d (MITM) by an actor “with a privileged network position.” The only exception to this rule are connections to a handful of sites for which browsers have “pinned” certificates. It is simple for hundreds (potentially thousands) of “privileged actors” to passively hijack ALL HTTPS connections and do so undetected as shown in the pseudo-code below:
function do_TLS_MITM(connection) {
if (
// let's not get caught by "pinning", shall we?
isPinnedSite(connection.website, connection.userAgent)
// never hijack those EFF nuisances, they're annoying
|| isOnBlacklist(connection.ip)
// hijack only 5% of connections to avoid detection
|| randomIntBetween(1, 100) > 5
)
{
return false;
}
return mitm_and_store_in_database(connection);
}
Certificate pinning cannot stop this type of mass-surveillance. It is a band-aid that some companies use to mitigate the problem for their specific applications. Pinning is a way to double-check the work that Certificate Authorities (CAs) are tasked with, but it cannot be an answer to this problem because it’s impossible for browsers to ship with the SSL certificates of all of the websites on the internet. Pinning certificates on “first encounter” is untenable from a user & sysadmin perspective.
This is where DNSChain and the dotDNS metaTLD come in.
What is a metaTLD?
*.dns (sometimes written “dotDNS” or “dot-DNS”), is a type of Top Level Domain (TLD) called a metaTLD. The key differences between a metaTLD and other types of TLDs are:
- metaTLDs do not resolve to the same IP for everyone. Instead, they resolve to an IP that you (the user) trust (and hopefully own).
- metaTLDs cannot be registered. You already own them.
okTurtles is a JavaScript application and browser extension that will facilitate secure, “NSA-proof” communication over existing websites like Facebook, Gmail, and Google+. In order to send a secure message, it needs the identity key for the person you’re communicating with, and it must be certain of that key’s authenticity (that it actually belongs to Alice and not to GCHQ/NSA/etc). This is the same problem that browsers and all TLS-based systems face.
Instead of relying on X509 PKI CAs, okTurtles asks a trustworthy DNSChain server (trustworthy because you chose it) using dotDNS.
What’s special about this approach and why does it make okTurtles actually “NSA-proof”?
- It does not rely on TLS for the answer, and therefore doesn't rely on the most untrustworthy of CAs out there.
- DNSChain, likewise, does not rely on CAs.
- Instead, DNSChain pulls its information from a locally stored blockchain (Namecoin currently, but any blockchain can be supported).
- The public key for the DNSChain server is pinned in the browser extension. This protects all of the answers that come from DNSChain (including DNS)!
Why a metaTLD?
Combining pinning with a hard-coded IP or a hard-coded URL would be to choose a centralized design, and that doesn't work for many (hopefully obvious) reasons. Using dotDNS allows answers to be looked up in a truly distributed, decentralized and secure database.1dotDNS makes it possible for JavaScript applications to securely query the blockchain (and potentially manipulate it) without needing to connect to the blockchain directly or store any information about the blockchain locally. Additionally, the dotDNS metaTLD always results in an answer from the DNSChain server that the user has chosen and declared trustworthy. The DNSChain server can even further protect and encrypt all of the DNS queries that their system makes, because it serves authenticated DNS in addition to authenticated HTTP(S).
Queries to Namecoin can be made over namecoin.dns. Want to know Alice’s public key? Easy, just load http://namecoin.dns/id/Alice and parse the signed JSON.
dotDNS also means that JavaScript applications can query the legacy DNS system over something like legacy.dns. This was not possible previously due to browser limitations.
Whom has your computer chosen to trust?
Your computer trusts "Root CAs" above all else. They're supposed to be like "the most trustworthy things on the planet."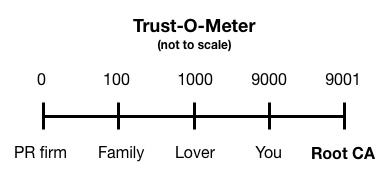
Figure 2. If you were to put Root CAs on a number line next to Mom, Dad, and your SO, this is where they’d fall according to X509 PKI.
Root CAs are able to create SSL certificates that will get browsers to show lock icons. They aren’t the only ones. In total:
"More than 1200 root and intermediate CAs can currently sign certificates for any domain and be trusted by popular browsers."http://www.ietf.org/mail-archive/web/therightkey/current/msg00745.html
How many Certificate Authorities have you invited over for dinner?
If you're like most people, the answer is zero. If you're like most people, you wouldn't have even heard of a CA before reading this post. And yet, to computers, they are like Gods: Infallible Speakers of The Truth™ (except when they're wrong).If you’re using OS X right now, actually go and try this right now:
- Open the Keychain Access application (use Spotlight to find it).
- Click on System Roots.
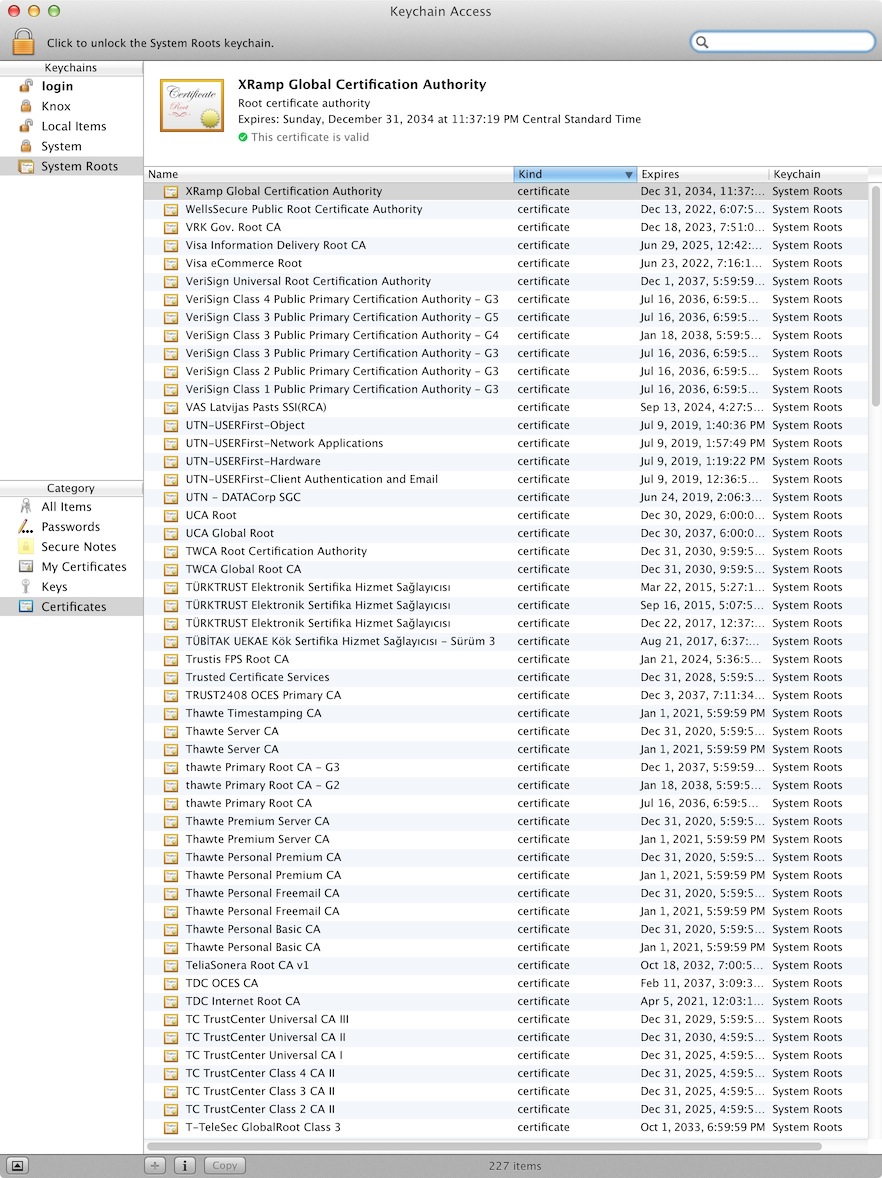
You should see something like this:
My apologies for my laptop’s screen. It wasn’t able to show the entire list of 227 Root Certificate Authorities that the operating system trusts for virtually all of its communications security.
Really, have a look:
- Who is "EBG Elektronik Sertifika Hizmet Sağlayıcısı"? I don't know how to pronounce that and yet apparently someone decided everyone (including me) must trust them with all of our online security?
- Who is "NetLock Halozatbiztonsagi Kft."? Maybe you know them? Why am I trusting their word that my connections are secure?
- I don't remember entrusting all my online communications to "AOL Time Warner Inc." either, but at least the name sounds familiar!
- "(c) 1999 VeriSign, Inc. - For authorized use only" Do you remember getting a letter or an email asking for your authorization to entrust them with the security of all of your online communications? I don't.
FAQ
- Has CA compromise happened? Yes.
- Is it hard to detect? Yes. (They are "valid certificates" after all!)
- Do companies pay money in exchange for said broken security? $200+ every year!
- Do we need CAs? Absolutely not. Nor do we need to pay for SSL certificates.
- What apps are affected by this problem?
- Apple's "secure" iMessages.
- The browser you are using right now and all of the websites you visit that have a "secure padlock icon" displayed (except for a few that might be pinned).
- Email. Including the "secure kind" that goes over "Secure" Socket Layer (SSL).
- Most "secure" connections on the internet.
- How long has the "security world" known about this problem?
- Some folks probably knew the day that SSL was invented, however, one of the first internet posts to offer a real solution to the problem is now over four years old, and the EFF's seminal blog post about the problem is just a tad under that.
- Will it continue to happen?
- Don't worry, bad things can only happen in the past, for up to four years, tops. After that, the bad guys give up their power voluntarily and Google saves us using "Certificate Transparency". We then get to pay for SSL certificates that don't really work but they make browsers show those lock icons that say things like "this connection is secure" so it's all good.
What you can do to help
- Keep yourself informed and follow @okTurtles and @DNSChain.
- Inform others and call out disinformation.
- Keep this problem in the public's conscience. Even the EFF, one of the first organizations to publicly recognize this problem, sometimes forgets about it and hands out green checkboxes to companies that implement "security features" that don't do anything to fix this problem, without so much as a mention that those features do not protect people from "privileged actors." This problem is
severala couple decades old and it's not magically going away, even if another million people sign your "Please stop spying on us!" online petition. - Help us with DNSChain and okTurtles.
- Implement a JavaScript app that uses DNSChain for authentication. If you must, you can even query a public endpoint like
dns.dnschain.net. - Run your own DNSChain server and share it with others. Help them set up theirs.
- Join the community:
Community forums + IRC channel
We're pleased to make several community related announcements today:- The okTurtles forums are live!
- The DNSChain Gitter channel.
Hacker News discussion : https://news.ycombinator.com/item?id=7324550
Donating = Loving!
You can empower our work by donating!