Also see our followup: How To Compromise Zcash And Take Over The World
As part of our work, we will sometimes put a new system under scrutiny in order to provide constructive feedback, and/or clear up a widespread misunderstanding that could lead to problems down the road (for example, see our series on Certificate Transparency).
Today, we continue this tradition by reviewing one of the lesser known details of the Zcash cryptocurrency. A few days prior to publication, we reached out to the Zcash team and asked them to review this post for accuracy. We thank them for subsequently posting more details about Zcash’s trusted setup.
Two Seemingly Innocuous Words: "Trusted Setup"
Zcash is different from other cryptocurrencies. It is different not just with respect to privacy but also with respect to its financial fundamentals (specifically, its monetary supply), in that they are not knowable with certainty.Type “zcash” into any search engine today and you’ll most likely stumble across this WIRED article. Like most coverage of Zcash, the WIRED piece fails to mention the Zcash Catch, otherwise known as its trusted setup.
Zcash relies on novel zero-knowledge proofs—specifically, non-interactive zero-knowledge proofs of the zk-SNARK variety—to power its privacy features. In principle, Zcash could work with many types of zero-knowledge proofs, but for efficiency reasons Zcash uses one that they say needs a trusted setup. That means you’ve got to trust that the Zcash team was able to set up the system properly.
What happens if they fail?
Someone can print as much money as they want, for free, and in total secrecy.
Given the "All coins are created equal" tagline, some might consider that to be kind of a big deal, deserving of at least a footnote somewhere. But this important detail can't be found on the z.cash website,1 nor in the media coverage about the project.Media Coverage of Zcash
We'd like to remind the news organizations out there that by covering cryptocurrencies you are effectively advertising a financial instrument. A failure to mention that the instrument comes with a serious catch is, at the very least, a serious breach of ethics, and at worst could potentially run you afoul of the law. (As decentralists who question the ethics of many laws, we are more concerned about the former than the latter, but this is a case where the law and ethics fall into alignment.)Even Zcash agrees that you should mention it!
HT to @zcashco for the RT, I'm impressed, that shows integrity. 👍 pic.twitter.com/EskgndX66B
— Greg Slepak (@taoeffect@crib.social) (@taoeffect) February 8, 2016
However, in fairness to the media, the Zcash team could also have done a better job being transparent about this quirk.
Zcash Must Improve Its Documentation
To be clear, most of our concerns regarding Zcash have more to do with how it presents itself, and less to do with its technical approach (although as we'll discuss, we hope for improvements in that area as well).Specifically, it is very concerning to us that the Z.cash website1 and the GitHub project page do not mention the implications of the trusted setup.
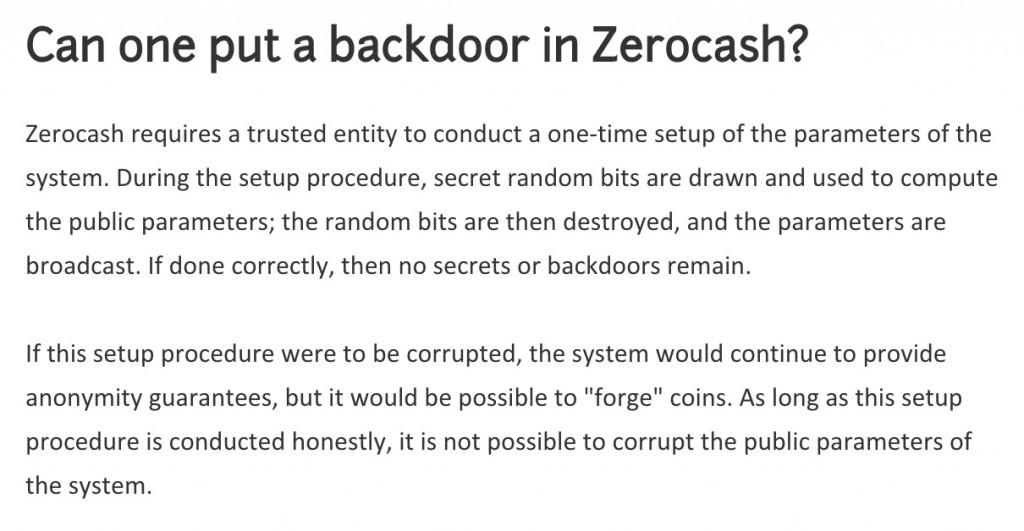
The FAQ on GitHub even contains highly misleading information:
Q. Will Zcash contain a backdoor?
Neither Zcash nor any other cryptographic algorithms or software we've made contains a backdoor, and they never will.
There are several serious problems with this answer. For one, the answer is contradicted by a nearly identical question in another Zcash project FAQ:That is from zerocash-project.org, an older site that visitors browsing the new z.cash domain will be unlikely to find.
The original answer is the one that should be on the GitHub. After all, Zcash requires trust to work, and hiding the details by using a slightly rephrased question doesn’t build confidence. The answer should also acknowledge that Zcash cannot guarantee that they will succeed in the trusted setup.
Another question asks:
Q. Is Zcash peer reviewed?
Yes.
Zcash is based on the peer-reviewed Zerocash protocol, which was published in the IEEE Security & Privacy conference in 2014. The Zerocash paper provides a detailed technical overview of the specification.
There is a difference between publishing a paper and peer-review. Outside of those involved with Zcash we've been unable to find peer-review that the entire approach—from the zk-SNARK implementation to the setup—is sound, and that's not from lack of trying. We've asked several of the brightest minds in the cryptocurrency space, and none feel confident enough to implement or teach zk-SNARKs, let alone vouch for the legitimacy of the trusted setup (the details of which were only recently revealed).It will require time for folks to get a sufficient enough grasp of zk-SNARKs before they can begin to evaluate the full safety and security of what Zcash is proposing to do.
Trusting The Trusted Setup
Unless Zcash addresses the lack of sufficient clarity and transparency in its communication, it would not surprise us if this approach generates comparisons to that of an elitist group of computer geeks asking the world to trust that they won't, either through intention or incompetence, end up swindling folks out of the magic Internet money Zcash is pushing.Why is the trusted-setup approach being taken seriously at all? This is for several reasons:
- The people behind the Zcash project include well known and respected names like Zooko Wilcox, Matthew Green, and others from highly regarded institutions like MIT, Johns Hopkins, U.C. Berkeley, etc.
- The Internet really needs the properties that Zcash wants to deliver (discussed below), and in principle what Zcash wants to do is possible.
- As we'll discuss next, the Zcash team has put incredible thought and effort into minimizing the risk associated with the trusted setup.
The trusted setup is described in dense technical detail in this 18-page paper. The overall gist is that it involves a group of some (currently unknown) number of people running a computer program on multiple machines. Assuming there are no flaws in the approach, if at least one those people manages to correctly follow the setup procedure on a computer that is not compromised, then Zcash should live up to its claim of having a knowable number of coins.
UPDATE August 27, 2016: However, this approach amounts to security theater. See the comments to this blog post.
The procedure is a one-time event, and the claim is that the only way it can fail is if every participant is either dishonest or is compromised in some manner.
Though we acknowledge that a lot of effort has been put into securing the trusted setup, it’s nevertheless important to ensure that every potential stakeholder in Zcash be informed about it, since:
- The trusted setup approach, still, ultimately asks that the world puts its faith into a small group of people, and therefore we feel it provides less of a guarantee about its overall monetary properties than other cryptocurrencies.
- The trusted setup may be unnecessary to achieve the desired privacy properties (see Monero vs Zcash and alternative or yet-to-be-discovered NIZKs).
The Power of Zcash
It would not be completely inaccurate to compare the cryptocurrency community's desire for zk-SNARKs/Zcash to Frodo's relationship with The Ring.
The Ring also gave Frodo privacy, but it came at a huge cost: it corrupted him.
Zcash makes it possible to hide the origin, destination, and value of a transaction in a very elegant and simple way. Just as it is easy to slip on a ring, it is easy to for users to use Zcash. That property is important for any serious digital cash system to flourish, as it protects the fungibility of the currency and the privacy of its users. After all, nobody wants every transaction that they make to reveal their entire financial story.
However, as we mentioned before, there are alternatives to using a trusted setup. Zooko does a great job comparing many of them. It’s not completely clear, however, that Zooko’s assessment of Zcash’s choice of zk-SNARKs and the supposed trade-offs with CryptoNote-based coins (like Monero and others), is entirely correct. For example, while Zooko’s post states that the amount of a transaction must be revealed in CryptoNote, this may not be true.
Also, as mentioned in the Zcash paper, there exist other zero-knowledge systems that could potentially be used (or invented) that do not require the trusted setup:
Bitcoin already uses zero-knowledge proofs in a way that doesn’t put into question the overall properties of the system, and reusable payment codes appear to be a promising privacy-preserving solution (although not as private as Zcash).
Unanswered Questions + The Zcash Catch-22
Should Zcash proceed with the trusted setup as-is, several important questions remain:- How many participants will there be and how will they be selected?
- During the setup, will they be in the same country or in different countries, within the Five Eyes or without?
- Will they all be part of the same clique or will they come from genuinely diverse backgrounds?
- Will there be full transparency (i.e. cameras, live broadcasts, public ceremonies), or will it be conducted in total secrecy?
- What assurance will there be that there really were X independent participants doing Y thing at Z time?
- And most importantly: will Zcash wait for an independent security audit of the trusted setup itself?
Our Message To Zcash
We deeply admire and respect your work and we hope it succeeds on its merits. At the same time, we feel that deploying Zcash at this stage, without transparency and without an independent audit of the implementation and the trusted setup, would be unnecessary and inappropriate. We also feel it is Zcash's responsibility to ensure that every potential user/investor in Zcash understands the implications of its trusted setup, and that requires going out of your way to inform them.Consider:
- Imagine selling Zcash's assets to a group of computer scientists that you don't know and letting them do the trusted setup. Would you still feel comfortable investing in Zcash? If the answer is no, you may want to reconsider your approach.
- It's in the interests of Zcash to verify that no better approach is possible. If a Zcash competitor accomplished the same thing, but without the trusted setup, it would very likely hurt the value of Zcash.
- Governments may already be wary of the privacy aspects of Zcash, so they could use issues like improper disclosure, false advertising, or fraud to go after you.
As when opening a bank account or purchasing insurance, it’s the seller’s responsibility to ensure that the buyer is able to make an informed purchasing decision. If the trusted setup is used, potential investors need to know that Zcash comes with several asterisks:
- The total number of coins in circulation is not guaranteed from the outset, and it may not be possible to know how many there are.
- If the trusted setup failed, then the value of the coin could be adversely affected by inflation.
- You use this product at your own risk, etc. etc.
Our gratitude to Zaki Manian, Vlad Zamfir, Alex Chepurnoy, Andrea Devers, and Simon Grondin for reviewing this post! You can follow the turtles and the author on twitter.
1 That sentence was written prior to the recent blog post, however we’ve decided to keep it as-is for now since the post is buried where most Zcash users/investors won’t see it and, even if they do, many won’t fully grok the implications of the trusted setup unless it’s written in clearly visible, simple terms.
Donating = Loving! You can empower our work by donating!